MAHWAH, NJ and HERZELIYA, ISRAEL--(Marketwired - Oct 12, 2016) - TopSpin Security, Inc., the leader in integrated deception and detection solutions, today announced the results of the Applying Deception Mechanisms for Detecting Sophisticated Cyber Attacks Report, a study investigating the performance of deception technologies in corporate environments. Professional hackers and security experts from across the globe participated in the research, which simultaneously included a variety of malware attacks.
The study revealed that private information stored in document files is the most popular target for attacks coming from professional hackers, as well as from malware. File traps, including Office files, recent docs and deleted docs, were touched the most accumulative times during the research. The next most attractive attack targets were application traps, consisting of session apps and browsers, followed by email traps. Notably, 100 percent of the attackers were detected during the initial stages of the attack during the study.
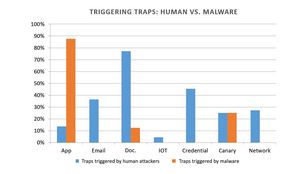
As far as trap types triggered by the hacker participants and malware, 90 percent of the application traps set were touched at least once, followed by 70 percent of the email traps and 64 percent of the document traps. However, it is interesting to note that the research revealed that human attackers and malware have very different targets they seek. While human attackers seek document files, malware and machine attacks target applications.
"This research is unique in gathering information about attack patterns of hacking experts and advanced malware, and the effectiveness of deception traps set in an enterprise," said Omer Zohar, Head of Research at TopSpin Security. "Attackers go after files not only to steal them -- but also in order to use information stored in files to get credentials and other types of data that helps them traverse through the network."
For a copy of the study, see: https://www.topspinsec.com/portfolio-items/applying-deception-mechanisms-detecting-sophisticated-cyber-attacks/
Other key findings of the research include:
- For the most popular traps triggered by human attackers, 77 percent of participants triggered document traps set in the enterprise environment. Next, 45 percent of the hackers triggered credential traps, consisting of usernames and passwords in files, directories and emails; followed by 36 percent who triggered email traps. In addition, human attackers also reached network, application and IoT-based traps.
- When it comes to malware attacks, application traps were the most attractive, successfully luring malware 90 percent of the time. Next, malware triggered 25 percent of the beacon traps in the environment, mechanisms built into a document or email file which send signals to pre-defined servers every time the file is opened. The third most popular attack targets for malware were document traps, 13 percent of which were triggered by malware.
- Passwords are the holy grail for attackers. The research showed that attackers not only picked up passwords regardless of their source (email, credman, lsass) or format (clear text, hashed, session ticket), they used the acquired passwords multiple times in a variety of locations. For example, attackers found an average of two credentials each, while each password was attempted an average of 2.5 times. In one instance, a password was used 11 times in 11 different places.
The Research Department at TopSpin Security conducted this study to investigate the efficiency of different deception technologies, as well as discover which other types of baits (decoys, mini-traps, beacon traps, "poisoned data") attract which type of attackers. Overall more than 50 professional hackers and security experts used their knowledge and skills to try to extract a pre-defined piece of data and stay undetected. The month-long experiment was conducted as a Capture the Flag (CTF) challenge, and simultaneously the environment was tested against a variety of malware programs. The research sample called for the best experts in the field -- red teams, pen testers and security researchers -- to participate.
TopSpin administered the study using its DECOYnet™ deception solution. The types of traps deployed by DECOYnet included file traps (documents, beacon traps, emails, logs, databases and recent/deleted documents); application traps (session apps including SSH and FTD, browsers app uninstall information); network traps (network table caches poisoning such as ARP and NetBios, mounted IoT devices including printers and cameras, open and half open connections to other decoys, and host and ImHost files); and credential traps (password and hash injections, Windows Credentials Manager and password managers).
DECOYnet is the industry's only deception-based solution with an integrated, full-fledged traffic analysis engine for continuously mapping organizations' network and assets, and assessing vulnerabilities for better deception placement and adaptation to changes in organizations' dynamic environments. Its powerful deception and egress analysis engines uniquely provide Intelligent Deception via strategically placed traps and decoys; Security Visibility detecting attackers' communication channels and illuminating network blind-spots; and Threat Analysis, correlating data from both the deception and visibility layers for additional security and dropping false positive rates to virtually zero. DECOYnet is the only solution to offer fully automated, point-and-click configuration of traps and decoys.
About TopSpin Security
TopSpin Security is the leader in integrated deception and detection technologies which allow organizations to quickly and accurately detect breaches, engage attackers and neutralize advanced cyber-attacks. Its technology is based on a network of decoys that lure attackers by mirroring valuable network assets and are fully adaptive to organizations' changing environments. Its unique traffic analysis engine and integration into organizations' existing security infrastructure deliver the industry's only deception solution that provides for strategic placement of traps and decoys; added security and internal correlation; and operational advantages such as automated, point-and-click configuration. Once engaged, the decoys interact with attackers, deceiving them and slowing their advances, while providing accurate, actionable alerts and forensics trails. TopSpin's DECOYnet is already deployed by leading Global2000 companies. The company's U.S. operations are headquartered in Mahwah, N.J., with its R&D center in Herzliya, Israel. Learn more at https://www.topspinsec.com.
TopSpin is a registered trademark of TopSpin Security, Inc., in the United States and other countries. All other brands, products, or service names are or may be trademarks or service marks of their respective owners.
Contact Information:
Contact:
Dan Spalding
(408) 960-9297